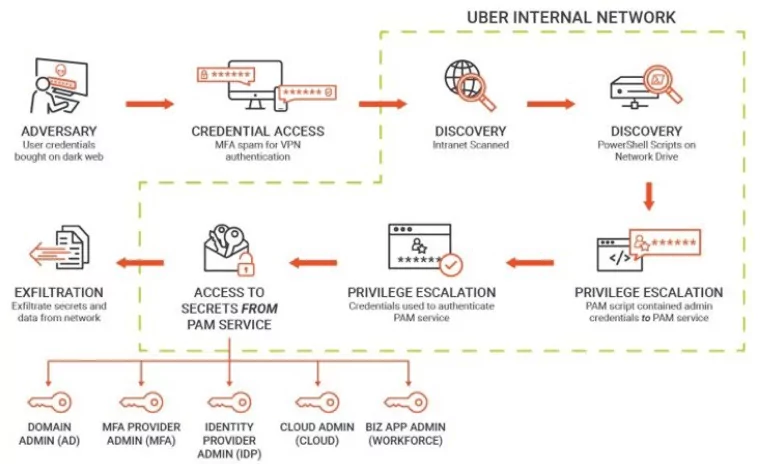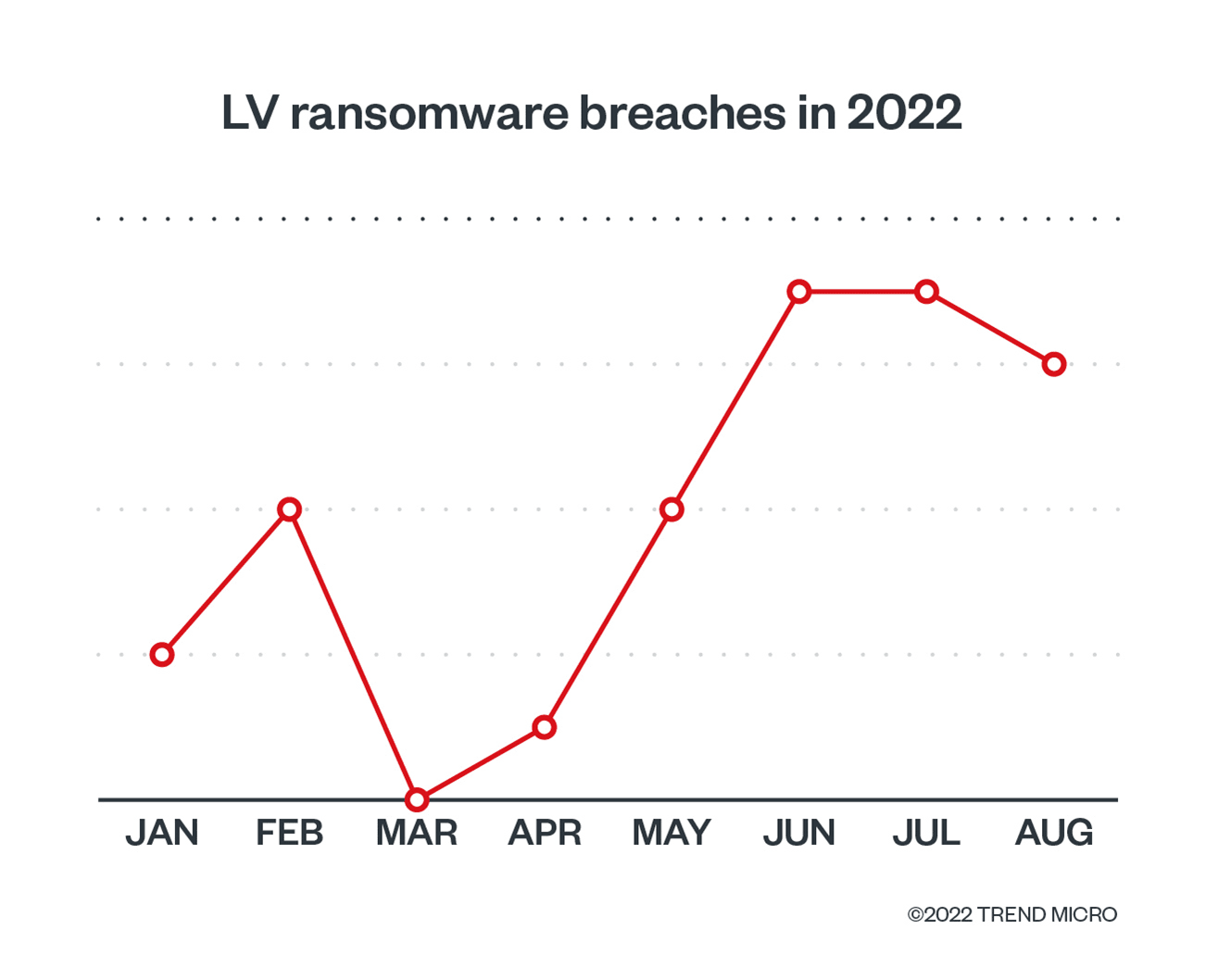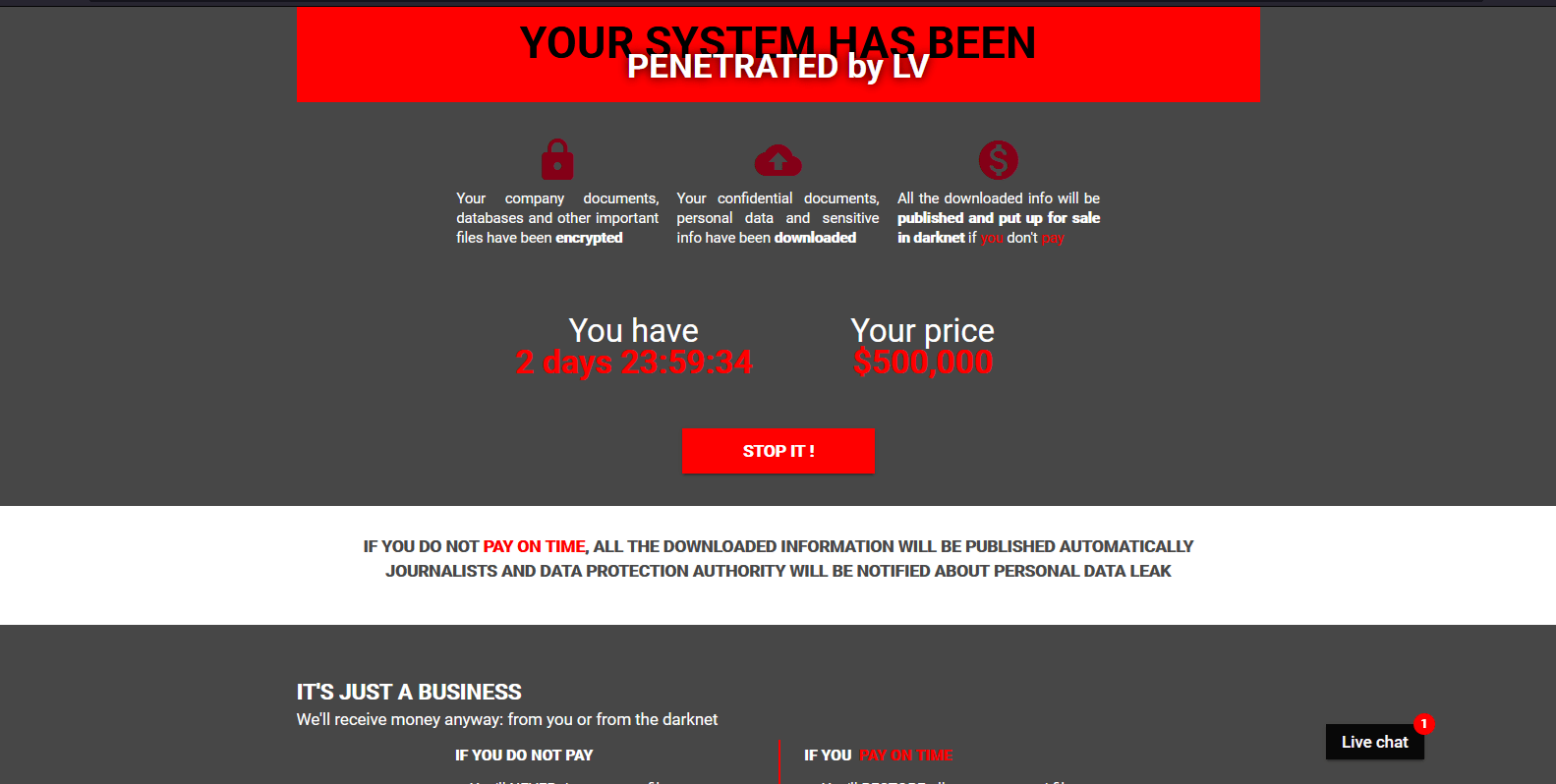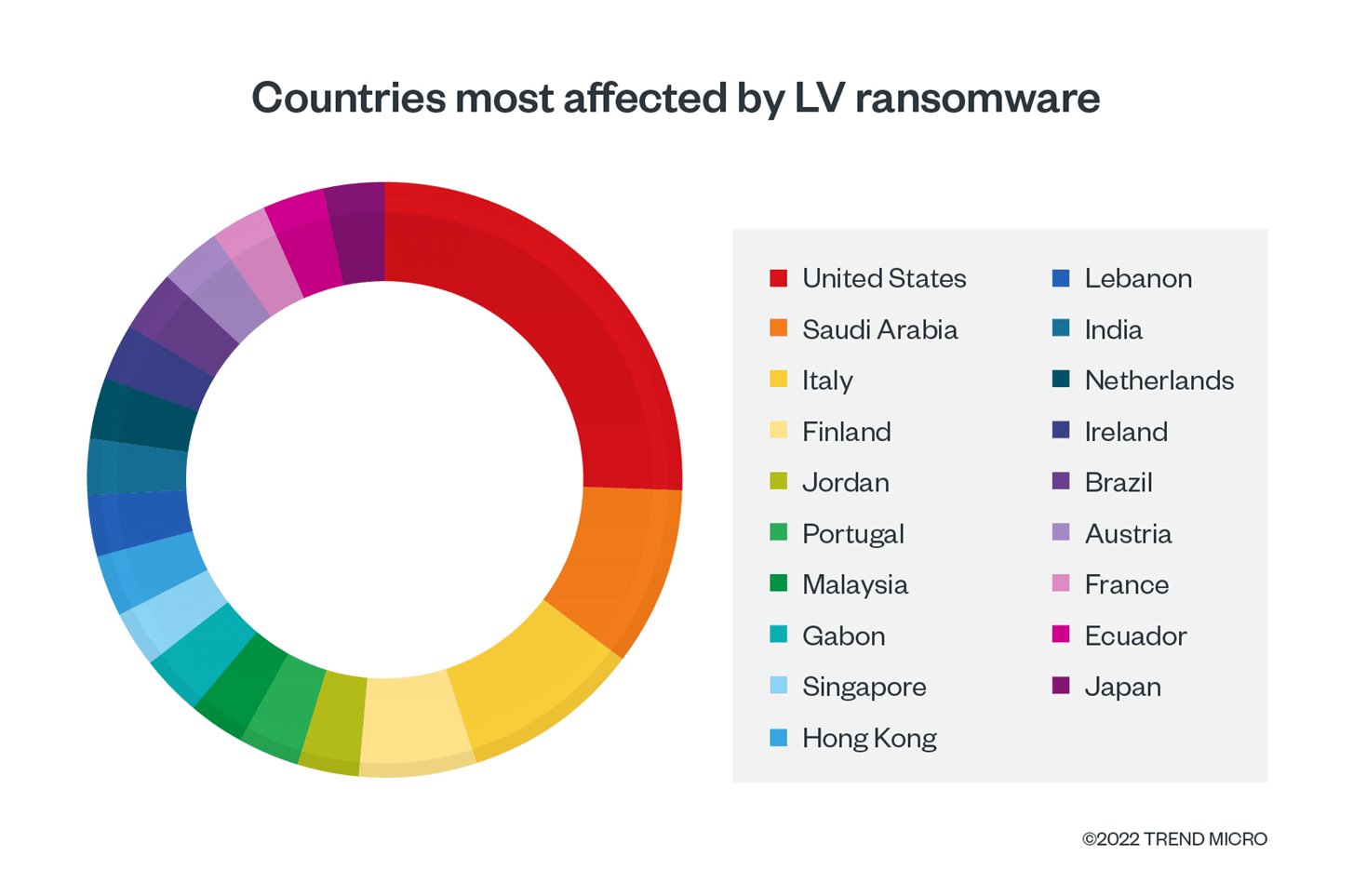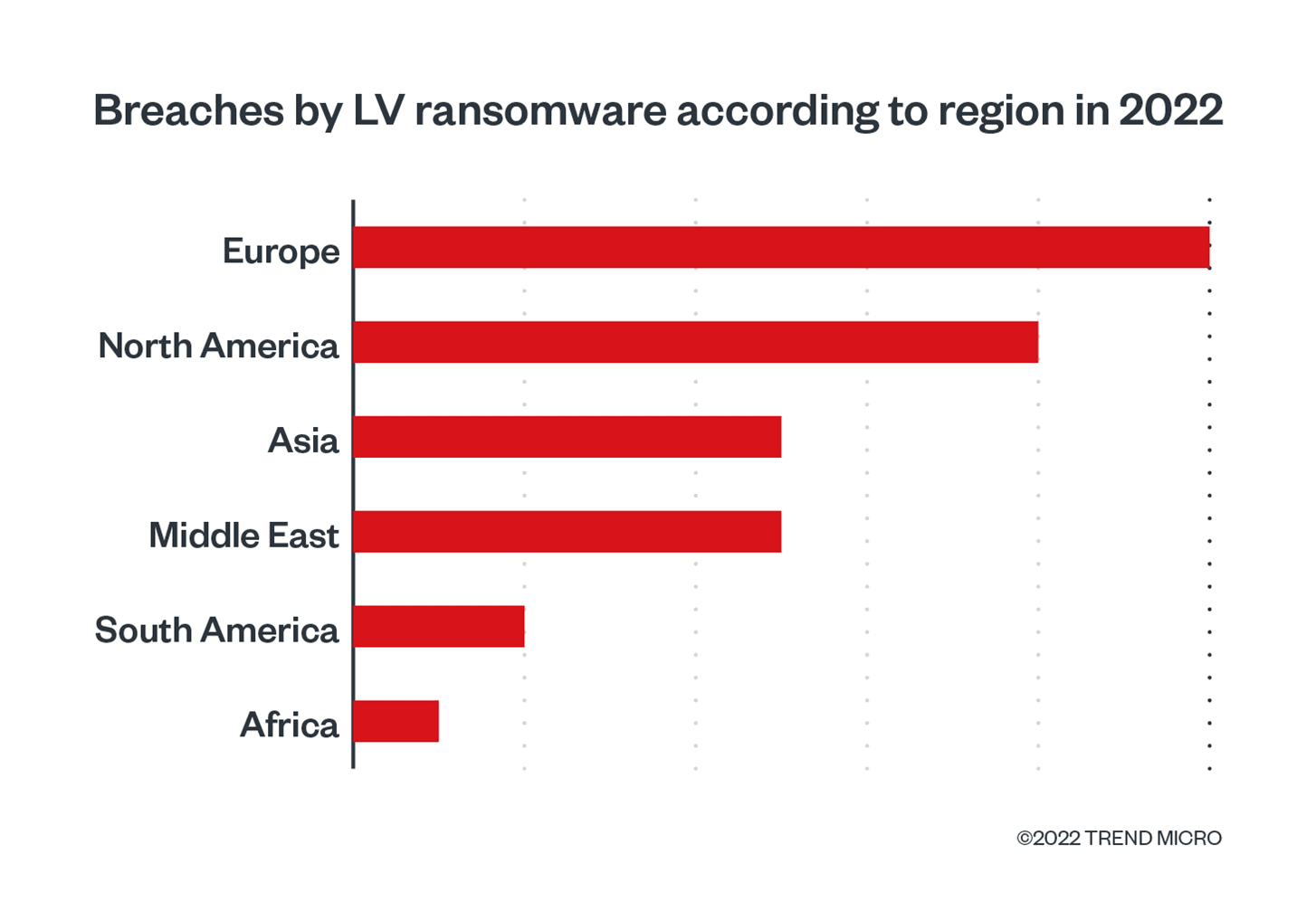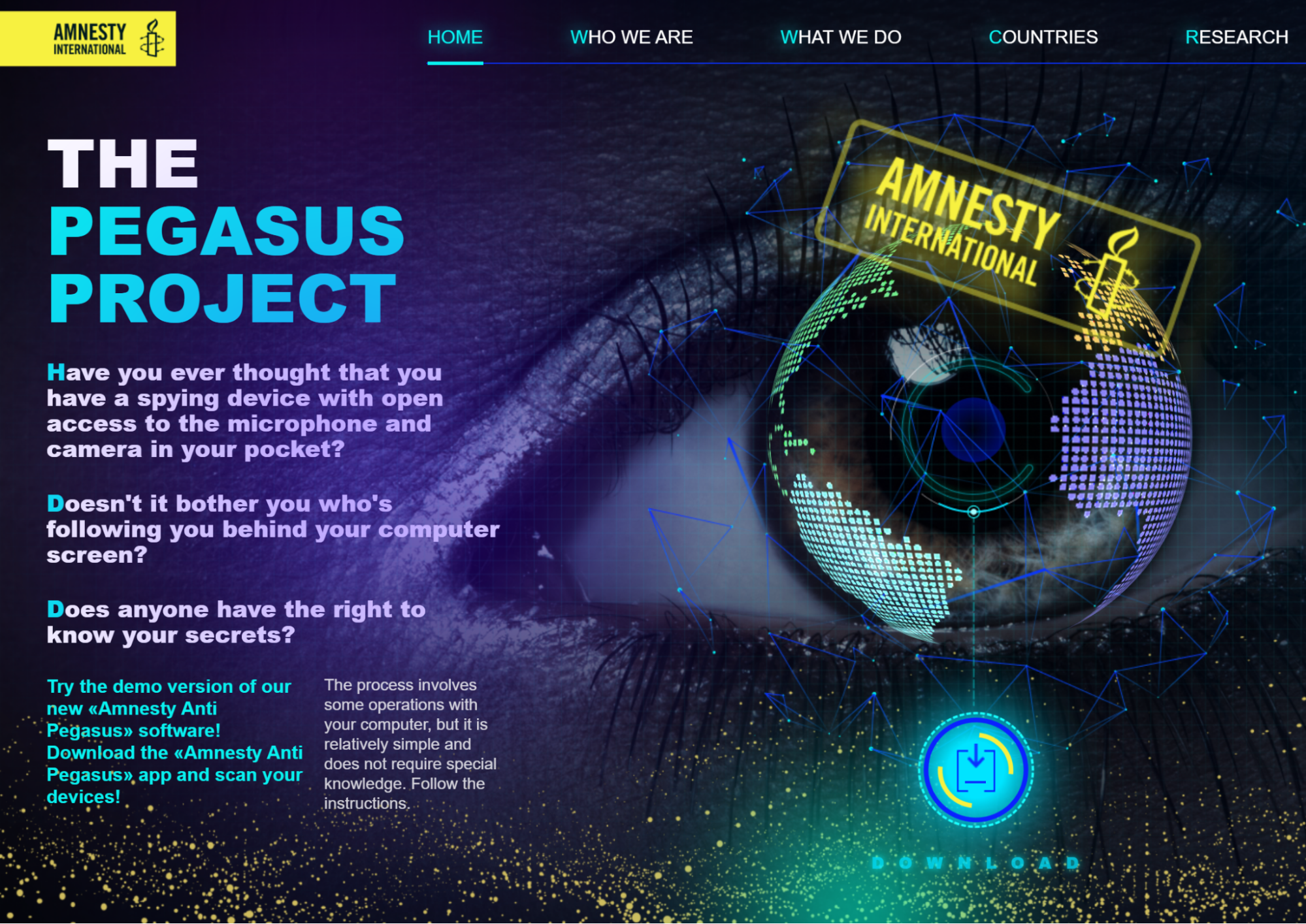
A wolf in sheep's clothing: Actors spread malware by leveraging trust in Amnesty International and fear of Pegasus
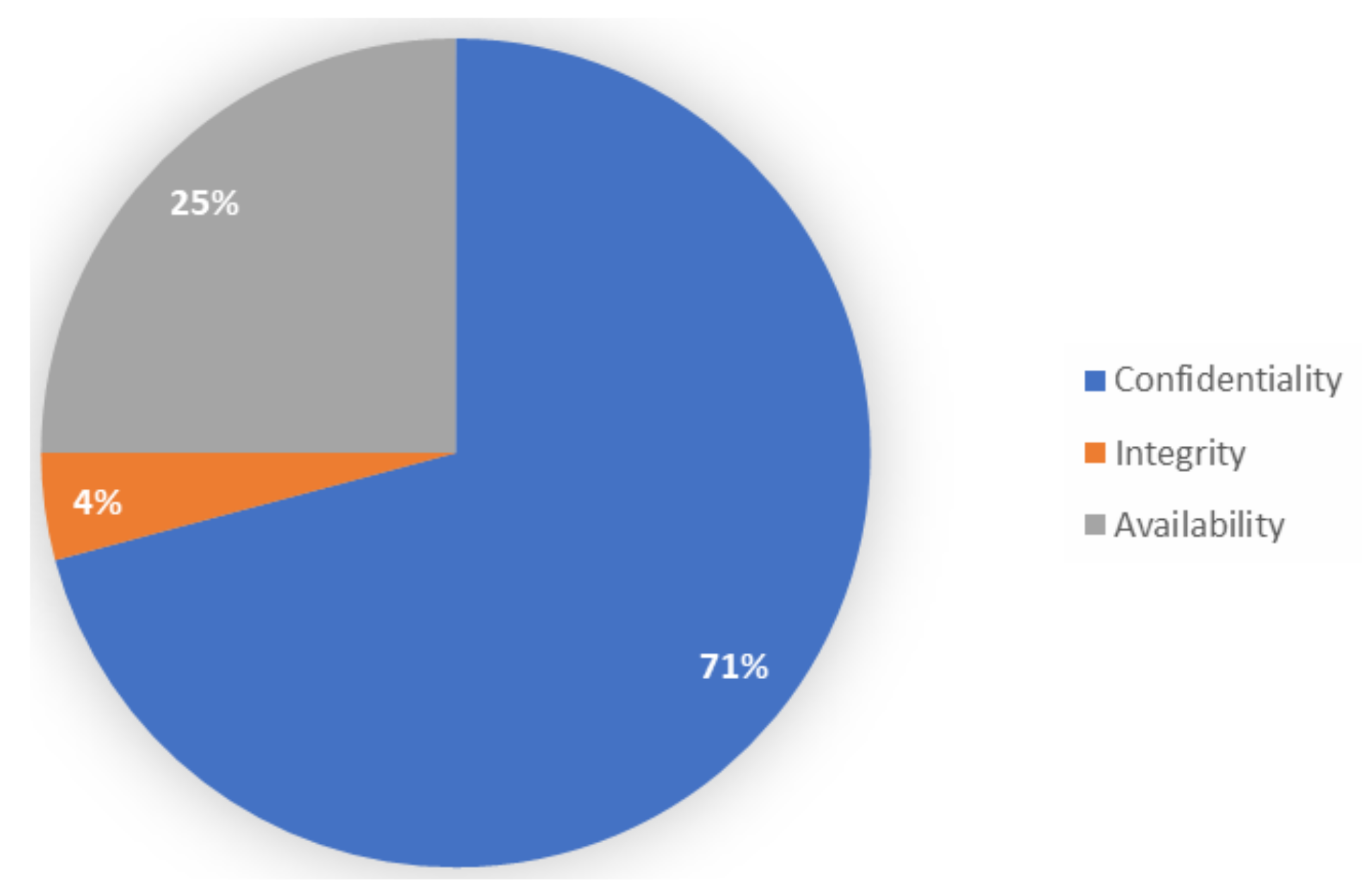
Information | Free Full-Text | Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends
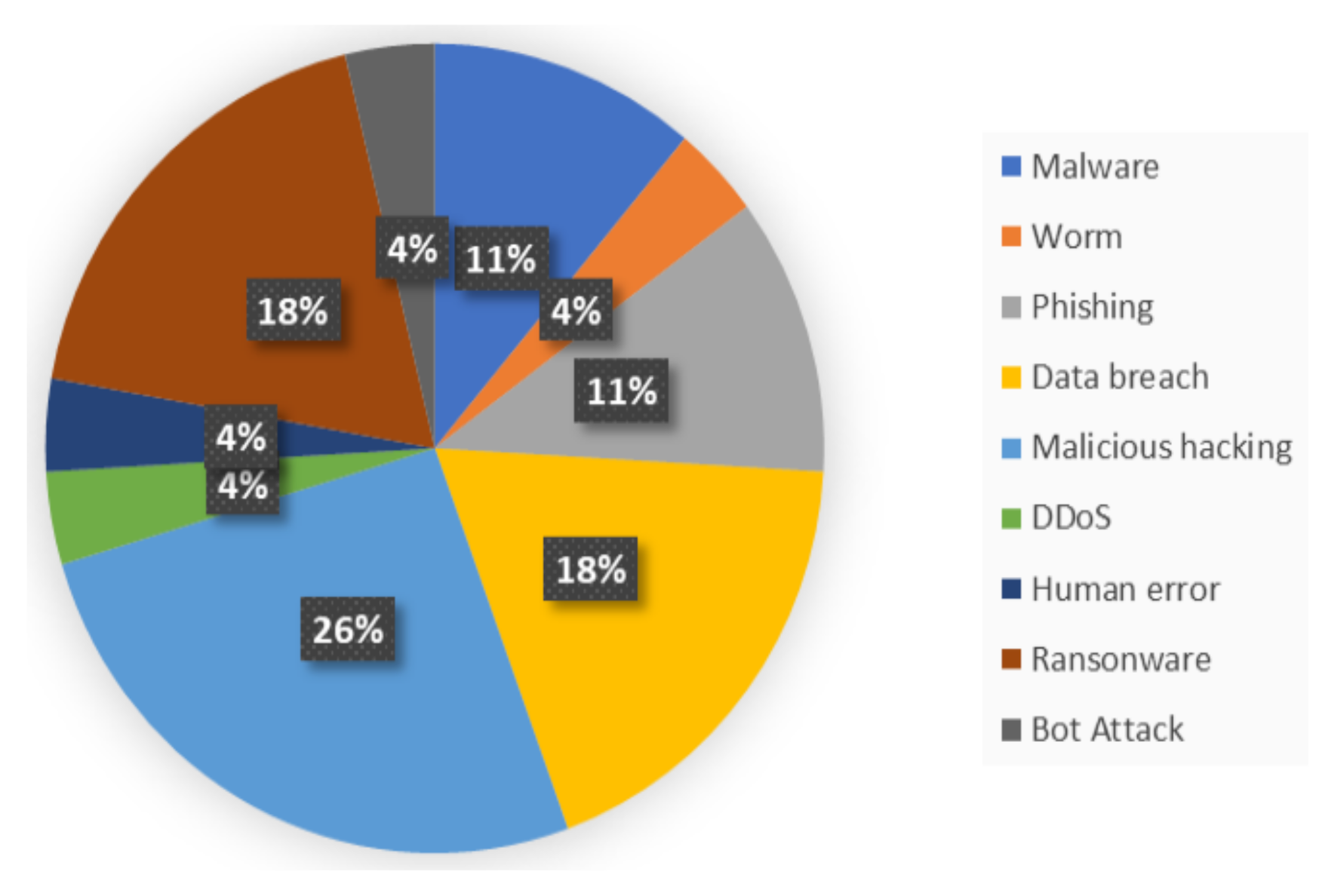
Information | Free Full-Text | Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends